Previous Level: Level 3
Theory
The communication between the client (our machine) and the server (that hosts the website) is done by a request-response. We sent a request for a certain page and the server sends the response with the content. Generally, they will follow different protocols and structures, which depend on the service. In this case, it is HTTP (Hypertext Transfer Protocol). The request generally includes the request method (GET, POST,…), the requested URL and the protocol version. However, it can also include additional, potentially needed information, through so-called request headers. There are many such fields, some more common than others. Relevant ones for this challenge are ‘Authorization’, which would include the credentials for the website and ‘Referer’, which is the URL/webpage from which the request is sent. Generally, all this is handled by our browser and we do not have to worry about it. It is however possible to manipulate requests.
Here is an example of an HTTP request of my blog that can be sent on the command line with curl:
| |
Every header is added in the same form: -H "Header-Name: Header-Value". The ‘User-Agent’ header shows information about the browser, and the ‘Accept’ header shows information about accepted response file types. The ‘purecookieDismiss’ is a header I programmed for this website.
If this would be sent over the command line, the response would be an HTML file/text.
There are many resources online, to read up on HTTP and its headers, for example Mozillas Developer Docs.
Solution
The page displays a text stating: ‘Access disallowed. You are visiting from "" while authorized users should come only from “http://natas5.natas.labs.overthewire.org/"’. Clicking the refresh link, the ‘visiting from’ will change to the natas4 website. The text seems to state that it is important from what page the link was requested. Meaning, we have to change the ‘Referer’ header to the expected site.
This can be solved in different ways with different tools. It might be possible to use the build-in browser tools or an add-on that allows for manipulating request headers. Or through command line tools or other special tools, such as Burp Suite.
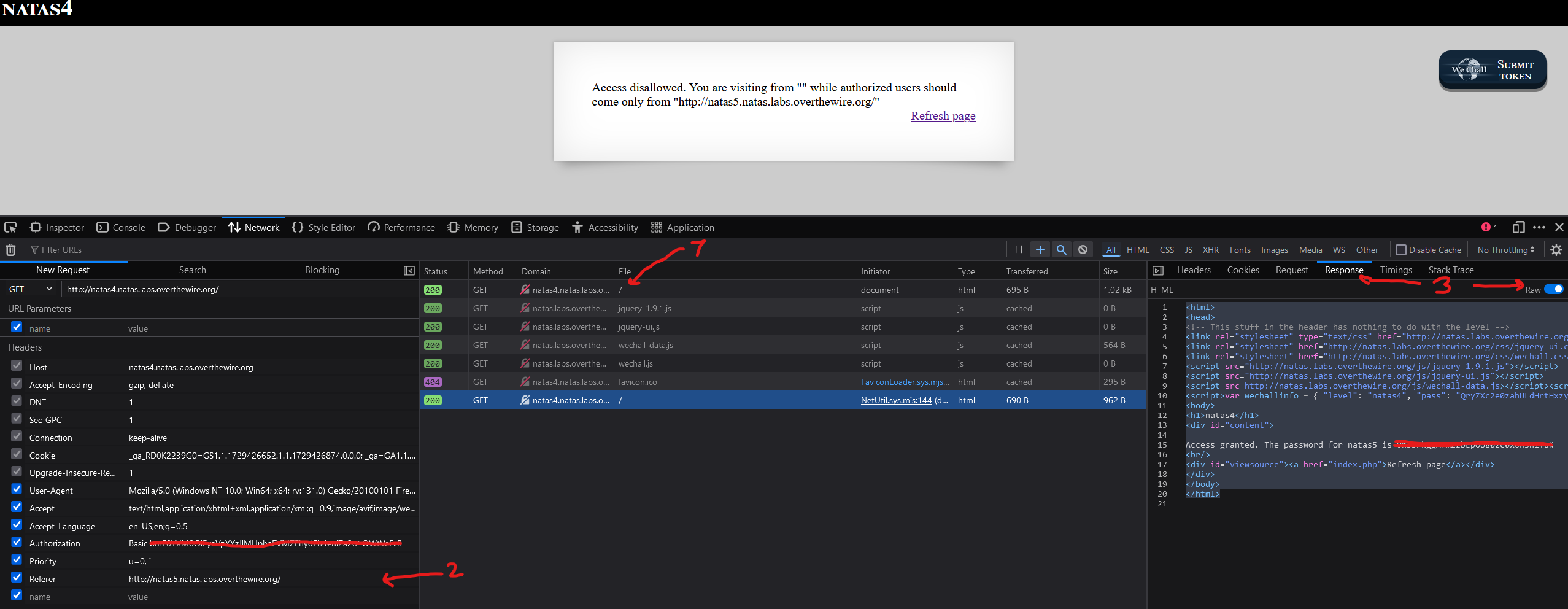
If the command line is used, the first step is to open the developer tools of the browser by pressing F12. Go to the network tab and refresh the website. Now you should see the requests that were sent. Clicking on the ‘index.php’ or ‘/’ file shows the headers, including the ‘Referer’ header. Right-clicking on this ‘index.php’ request will show an option called ‘Copy Value/copy as cURL’. This will copy the request in curl form. It is nice because it includes all important headers, specifically the ‘Authorization’ one, which is the ‘username:password’ in base64. The command then only needs to be edited. Simply replace the ‘4’ in the ‘Referer’ URL with a ‘5’ and send the curl request. If it is not included, then you can add it by using the same format as the other headers: -H 'Referer: http://natas5.natas.labs.overthewire.org/'. Alternatively the curl command can be constructed by hand as well.
Here is a shortened/redacted example of the curl command:
| |
If you use Firefox, you can right-click on the main request (‘index.php’ or ‘/’), select ‘Edit and Resend’ and then either edit or add the ‘Referer’. Once sent, select the new request, select the ‘Response’ tab, toggle the ‘Raw’ button and it will return the same raw HTML as the command line:
| |
This includes the password.
Here is an image of the developer tools with the correct tabs open:
https://overthewire.org/wargames/natas/natas4.html
Next Level: Level 5